
In today’s world, where data security is a top priority, protecting information as it moves between databases and applications is critical. Oracle GoldenGate, as a powerful real-time data replication platform, ensures that your data remains secure at rest, in transit, and during access.
With its Microservices Architecture and comprehensive security controls, GoldenGate provides built-in authentication, encryption, and compliance features to meet enterprise-grade security standards. In this blog, I’ll explore at a high level how Oracle GoldenGate secures your data and the best practices you can implement to enhance security in your deployments.
Key Security Areas in Oracle GoldenGate
Oracle GoldenGate takes a multi-layered security approach, covering:
- Data at Rest: Encrypting trail files and cached data
- Data in Transit: Securing communication between GoldenGate instances
- Access Control: Managing authentication and authorization
- Auditing & Compliance: Tracking security events and meeting industry standards
By implementing strong encryption, access control mechanisms, and secure authentication, GoldenGate ensures your data is protected at every step.
Securing Access: Authentication & Authorization
Access control in GoldenGate is managed using Role-Based Access Control (RBAC) and multiple authentication options.
Authentication Methods:
- Credential Store: Used to securely store database and network credentials, reducing the need to specify sensitive information (such as usernames and passwords) in parameter files.
- Certificates: Supports client authentication using TLS/mTLS for secure communication.
- TLS Support:
- Oracle GoldenGate supports Transport Layer Security (TLS) to encrypt data in transit between different components (Extract, DistPath, Replicat, Admin Server, Distribution Server, Receiver Server, and Database).
- mTLS (Mutual TLS):
- GoldenGate supports Mutual TLS (mTLS), where both client and server authenticate each other using digital certificates.
- This is crucial for zero-trust security models and for preventing unauthorized access to replication streams.
- TLS Support:
- External Identity Providers: Integrates with OAuth2, OpenID, IAM (OCI), and OAM (On-Premise) for centralized access management.
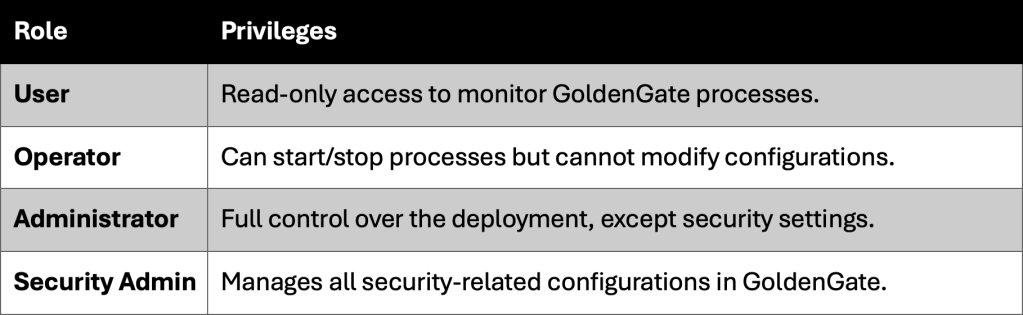
Role-Based Access Control (RBAC)
Oracle GoldenGate enforces strict role-based permissions, ensuring users only have access to what they need.
Best Practice
- Use the least privilege access control principle, which outlines that the user should have the minimum necessary privileges to access information required to do their jobs and enforce strong password policies for all accounts.
Protecting Data at Rest
GoldenGate ensures that trail files and persisted data remain secure on disk by using AES encryption with a robust Key Management System (KMS).
Encryption Options for Data at Rest
- Local Wallet: Encrypts data using an internal wallet.
- Oracle Key Vault (OKV): Recommended for on-premises encryption.
- Oracle Cloud Infrastructure (OCI KMS): Best for cloud-based deployments.
Best Practice
- Use an external KMS (OKV/OCI KMS) for stronger encryption key management and to comply with regulatory standards.
Securing Data in Transit
Oracle GoldenGate encrypts data while it is transmitted over the network to prevent man-in-the-middle attacks.
How GoldenGate Protects Data in Transit
- TLS (Transport Layer Security): Encrypts client-server communications.
- mTLS (Mutual TLS): Enforces two-way authentication using certificates.
- Secure WebSockets (WSS): Ensures encrypted data streaming.
- Reverse Proxy with Nginx: Encapsulates URLs and allows secure access via a single port (443).
Best Practice
- Enable mTLS for all GoldenGate communications to enforce authentication and encryption at both connection ends.
Auditing and Compliance
GoldenGate includes built-in auditing and logging to help organizations meet compliance standards and detect potential security threats.
Auditing Features:
- Auditing is enabled by default: All key security-related events are logged.
- Syslog Integration: Logs can be redirected to system security logs for centralized monitoring.
- REST API Logging: Tracks all API interactions for auditing.
Compliance with FIPS 140-2
- Oracle GoldenGate is FIPS 140-2 Level 1 compliant, ensuring that all cryptographic operations meet government security standards.
Best Practice:
- Regularly monitor audit logs and configure alerts for suspicious activities.
Secure Database Authentication & Authorization
Oracle GoldenGate securely connects to databases using the USERIDALIAS parameter, which prevents storing plain-text credentials in parameter files.
Additional Security Enhancements:
- Kerberos Authentication: Supports OS-level authentication for Oracle databases.
- Encrypted Database Connections: TLS-secured connections prevent unauthorized access.
- External Credential Store Plugin: Interface to the outside vault that stores the database password for the DB login. (e.g., CyberArk and HashiCorp)
Best Practice:
- Use USERIDALIAS instead of hardcoded credentials to protect sensitive database login information.
Key Takeaways
- Always use mTLS for secure communication.
- Enable Role-Based Access Control (RBAC) to manage user permissions.
- Encrypt all trail files using Oracle Key Vault or OCI KMS.
- Monitor audit logs for security incidents.
- Keep GoldenGate software updated with the latest security patches.
Final Thoughts
Security in Oracle GoldenGate isn’t just an option; it’s a necessity. With features like strong encryption, flexible authentication options, and built-in compliance tools, GoldenGate makes it easier for organizations to protect their data at every stage of the replication process.
By following best practices like enabling mTLS, using external Key Management Services, and enforcing RBAC, you can fortify your GoldenGate deployment and ensure your data remains secure and compliant at rest or in transit.
Leave a comment